
Elementor 3.6.3 Patches Critical Remote Code Execution Vulnerability
…Full post on WP Tavern
Read Full

…Full post on WP Tavern
Read Full

Welcome to Press This, the WordPress community podcast from WMR. Here host David Vogelpohl sits down with guests from around the community to talk about the biggest issues facing WordPress developers. The following is a transcription of the original recording. .redcircle-link:link { color: #ea404d; text-decoration: none; } .redcircle-link:hover { color: #ea404d; } .redcircle-link:active { color: #ea404d;…

In this episode we interview three attendees, one in India, one in Spain, and one in the USA. We have a great conversation about what it means to “attend” a virtual event, and ways we could make it more engaging for those that wish it. In this particular we’ll meet attendees Hari, Nilo, and Jeff….

WordPress allows you to build your website easily and opens up access to a whole world of stunning themes and powerful plugins. If you’re looking for a way to grow your business with a website, WordPress is the ultimate solution. There are ample online marketing techniques that allow you to scale your website traffic. However,…
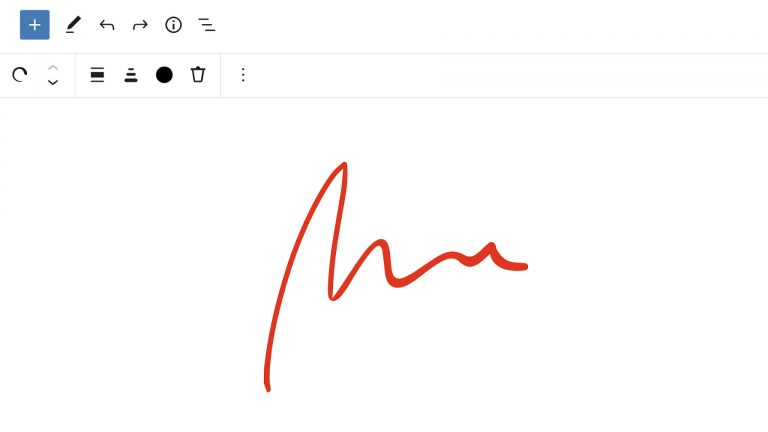
Automattic released a new plugin titled Sketch Block earlier today. It is a one-off block that allows end-users to draw directly in the editor. The plugin is marked as a beta release and requires Gutenberg to be activated to use. It is a part of the company’s Block Experiments project. To be perfectly honest, I…

WordPress.com is now selling a 100-year plan, one of the longest available in the industry, for a one-time payment of $38,000. It includes managed WordPress hosting (whatever that looks like in 100 years), multiple backups across geographically distributed data centers, submission to the Internet Archive if the site is public, 24/7 dedicated support, and a…

Welcome to Press This, the WordPress community podcast from WMR. Each episode features guests from around the community and discussions of the largest issues facing WordPress developers. The following is a transcription of the original recording. .redcircle-link:link { color: #ea404d; text-decoration: none; } .redcircle-link:hover { color: #ea404d; } .redcircle-link:active { color: #ea404d; } .redcircle-link:visited {…